Regain Control and Confidence
Cloud computing is the delivery of hosted services, including software, hardware, and storage, over the Internet. The benefits of rapid deployment, flexibility, low up-front costs, and scalability, have made cloud computing virtually universal among organizations of all sizes, often as part of a hybrid/multi-cloud infrastructure architecture.
Cloud security refers to the technologies, policies, controls, and services that protect cloud data, applications, and infrastructure from threats.
Cloud security is the protection of data stored online via cloud computing platforms from theft, leakage, and deletion. Methods of providing cloud security include firewalls, penetration testing, obfuscation, tokenization, virtual private networks (VPN), and avoiding public internet connections. Cloud security is a form of cybersecurity.
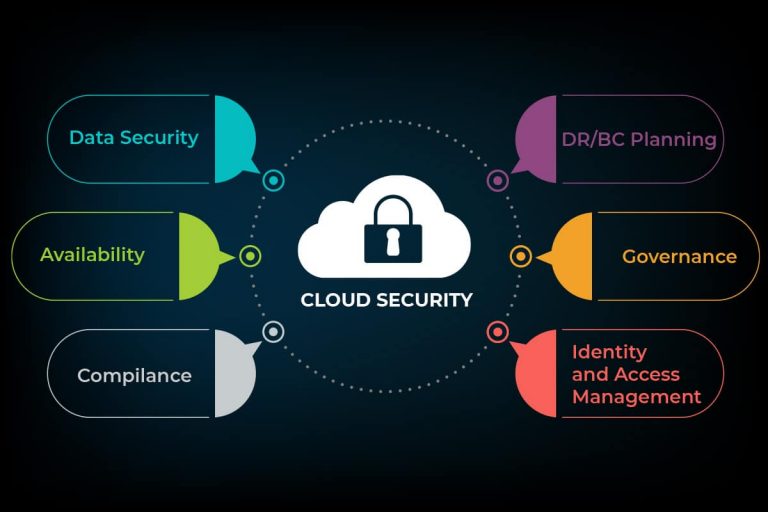
Like any computing environment, cloud security involves maintaining adequate preventative protections so you:
- Know that the data and systems are safe.
- Can see the current state of security.
- Know immediately if anything unusual happens.
- Can trace and respond to unexpected events.
Hackers run rampant in the modern world. Moving your business to the cloud puts you at risk of being targeted by hackers, so protecting yourself and your data is our priority.
openQRM is built with the customer’s safety in mind. Your data is precious and we understand that. Protect yourself against Ransomware
The openQRM Platform keeps your data safe using in-built security protocols and Plug-In Functions.
Cloud security is the protection of data, applications, and infrastructures involved in cloud computing. Many aspects of security for cloud environments (whether it’s a public, private, or hybrid cloud) are the same as for any on-premise IT architecture.
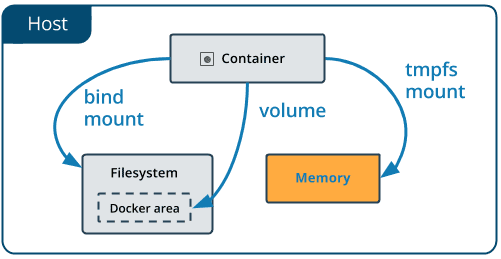
TMPFS Plug-In
Tmpfs is a file system which keeps all of its files in virtual memory.
Everything in tmpfs is temporary in the sense that no files will be created on your hard drive. If you unmount a tmpfs instance, everything stored therein is lost.
openQRM’s TMPFS Plugin gives the user the ability to boot images from memory resident. This means that you can safely reboot your server and all your VM and processes will run on it’s own.
This plugin can be used in the threat of a data breach or hacking attack, simply trigger a reboot and your data will be protected.
SSHTERM Plug-In
SSHTERM Plug-In allows you to securely login to your openQRM Web Interface. This prevents hackers from Hijacking your login attempts.
SSHTerm is a fully-featured Java SSH terminal that provides a whole range of features including port forwarding, password and public-key authentication, full clipboard support, record and playback input/output, and the ability to load/save connection settings to a file. The SSH terminal is now seamlessly integrated with a secure VNC viewer, a port forwarding manager, and a full SFTP client.


KVM Virtualisation Plug-In
KVM uses a combination of security-enhanced Linux (SELinux) and secure virtualization (sVirt) for enhanced VM security and isolation. SELinux establishes security boundaries around VMs. sVirt extends SELinux’s capabilities, allowing Mandatory Access Control (MAC) security to be applied to guest VMs and preventing manual labeling errors.
KVM (for Kernel-based Virtual Machine) is a full virtualization solution for Linux on x86 hardware containing virtualization extensions (Intel VT or AMD-V). It consists of a loadable kernel module, kvm.ko, that provides the core virtualization infrastructure and a processor specific module, kvm-intel.ko or kvm-amd.ko.
KVM Virtualisation allows you to utilise KVM tools and hardware, allowing for a high-security operation.
You can safely and securely execute VMs without the threat of acker bypass.